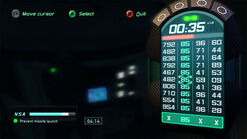
Splinter Cell agent Sam Fisher hacks an on-board computer on a missile. Note that the player has 'frozen' the correct numbers in the second column.
- "Hacking is performed directly on objects that can be hacked. Hacking allows you to access otherwise inaccessible information."
- ― Tom Clancy's Splinter Cell: Double Agent (Version 1) manual
Hacking is a gameplay feature in Splinter Cell: Chaos Theory, Splinter Cell: Double Agent (Version 1) and Splinter Cell: Double Agent (Version 2). Similar to lock picking, hacking is a mini-game that is performed by the player in order to complete objectives or optional objectives and tasks available to do. Hacking has various different outcomes, depending on what is currently being hacked. It can be used to view restricted content, such as emails or security camera video feed, or for unlocking doors and activating electronic-based systems.
Overview[]
In Splinter Cell: Chaos Theory and Double Agent (Version 1) both have the same hacking gameplay, the only difference is that Double Agent adds in additional upgrades that will allow players to hack computers faster.
- The hacking interface is composed of four columns and a valid code line of four numbers at the bottom.
- A timer at the top gives the amount of time before the hacking attempt fails. If the hack fails, an alarm will be triggered.
- Two warning lights at the top indicate the number of attempts the player can make before failing the attempt and triggering an alarm.
- Each column determines one of the four code elements. The player must find the four correct code elements and hack the system.
- The hacking device will automatically search for the correct door. Each time it finds a potentially valid number in one of the columns, it will freeze it. Once a column is composed entirely of frozen numbers, it will be validated and one of the four code elements will be validated.
- This process might take longer than the authorized time given by the timer at the top. You can speed up the process by manually validating a frozen number by using the highlighted cursor, which can be moved up and down and left and right in all the columns. Select a number and press the [Action] button to validate it. If it is a frozen code element, the column is immediately validated and it appears in the code element screen. If it was an un-frozen number the entire column is reinitialized and a warning light is triggered.
- When all the code elements are validated, the hack is successful.
- You can abort a hacking attempt at any time by pressing the [Back] button.
- Failing a hack attempt or aborting when the time is in the red zone will sound an alarm.
